In the fast-paced world of retail, where digital systems power everything from inventory to customer checkouts, a single vulnerability can lead to massive fallout. The Marks and Spencer TCS cyberattack in April 2025 highlighted this risk, costing the British retailer an estimated £300 million in lost profits and disrupting operations for months. What started as a deceptive phone call—hackers impersonating executives to request password resets—exposed critical flaws in password policies and third-party IT partnerships. As businesses grapple with evolving threats, this incident urges a reevaluation of how we handle access credentials in an era of sophisticated social engineering attacks.
- The Marks and Spencer TCS Cyber Attack: A Timeline of Events
- TCS’s Role and the Contract Termination Controversy
- Why Social Engineering Beats Traditional Defenses
- Flaws in Current Password Policies Exposed
- Rethinking Password Policies: Practical Steps for Businesses
- Lessons from the Marks and Spencer TCS Cyber Attack
The Marks and Spencer TCS cyberattack not only shook the retail sector but also sparked debates on outsourcing security and the human element in cybersecurity. With hackers from groups like Scattered Spider exploiting simple tricks to bypass defenses, companies must adapt or face similar devastation. This article dives into the details of the breach, its implications, and actionable steps to strengthen password protocols.
The Marks and Spencer TCS Cyber Attack: A Timeline of Events
The breach unfolded over the Easter weekend in April 2025, when Marks & Spencer (M&S) first noticed irregularities in its IT systems. What began as minor glitches in contactless payments and online ordering quickly escalated into a full-scale ransomware attack. By April 22, M&S alerted the London Stock Exchange about a “cyber incident” that had encrypted key servers, halting digital operations across stores and e-commerce platforms.
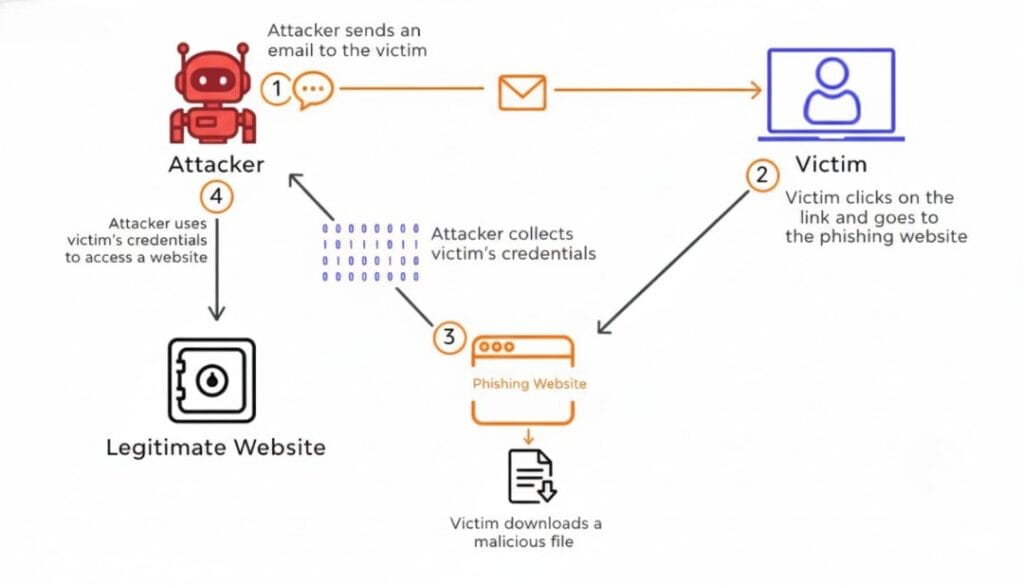
Investigators linked the attack to Scattered Spider, a notorious hacking collective known for targeting large corporations through social engineering. The entry point? A fake phone call to the IT service desk, managed by Tata Consultancy Services (TCS), M&S’s long-term Indian outsourcing partner. Posing as senior M&S executives, the attackers requested password resets, using publicly available information to verify their identities. This “vishing” tactic—voice-based phishing—granted them access to employee credentials, allowing ransomware deployment that locked down supply chains and customer data systems.
The impact was immediate: Shelves went bare due to disrupted stock management, online sales ground to a halt, and manual processes like pen-and-paper ordering became the norm. Customer details, including names and birth dates, were compromised, though financial data remained safe. Recovery efforts extended into July, with M&S forecasting a £300 million profit hit for the 2025/26 fiscal year—partially offset by insurance.
TCS’s Role and the Contract Termination Controversy
TCS, which had handled M&S’s IT helpdesk for over a decade in a deal worth up to $1 billion, came under scrutiny as the potential weak link. Reports suggested the compromised credentials originated from TCS staff, enabling hackers to move laterally into M&S networks. The Indian IT giant launched an internal probe, scanning systems and denying any fault, stating it does not provide cybersecurity services to M&S.
In July 2025, M&S terminated the service desk contract following a competitive tender process initiated in January—predating the attack. Both companies insist the decision was unrelated to the breach, with TCS calling media reports “misleading” and emphasizing the RFP’s independent nature. However, the timing fueled speculation, especially amid similar attacks on TCS clients like Co-op and Harrods. UK lawmakers, including the Business Select Committee, called for greater transparency on outsourcing risks.
On social media, discussions highlighted concerns over offshore IT vulnerabilities, with users questioning the balance between cost savings and security. TCS continues to support M&S in other areas, like data centers, but the incident has prompted broader industry audits of vendor partnerships.
Why Social Engineering Beats Traditional Defenses
The Marks and Spencer TCS cyberattack wasn’t about cracking complex code—it was about exploiting human trust. Scattered Spider, often comprising young, English-speaking hackers, uses vishing to manipulate helpdesk agents. By spoofing caller IDs and crafting urgent scenarios, they bypass multi-factor authentication (MFA) during reset processes.
This tactic evades firewalls and antivirus software, focusing instead on “knowledge-based” verification questions that rely on easily researched details. In outsourced environments like TCS’s, high-volume call handling can amplify risks, as agents juggle multiple clients and may overlook red flags.
Similar breaches at MGM Resorts and Caesars Entertainment show Scattered Spider’s pattern, now expanding to sectors like aviation. A 2025 Verizon report notes that 81% of breaches involve weak or stolen credentials, underscoring the need for change.
Flaws in Current Password Policies Exposed
Traditional password policies—mandatory resets every 90 days, simple Q&A verification—proved inadequate in the Marks and Spencer TCS cyber attack. Forced resets often lead to weaker passwords due to user fatigue, while phone-based verifications are ripe for impersonation.
Password reuse across accounts compounds the issue, allowing attackers to leverage data from past leaks. In this case, the “one fake call” exploited these gaps, turning a routine helpdesk interaction into a £300 million disaster.
Rethinking Password Policies: Practical Steps for Businesses
To prevent future incidents like the Marks and Spencer TCS cyber attack, organizations must modernize their approaches. Here’s a roadmap:
- Adopt Passkeys and Passwordless Authentication: Replace static passwords with device-bound passkeys from providers like Apple or Google. These require physical confirmation, eliminating phishing risks.
- Enhance Reset Verification with Zero-Trust Models: Use adaptive MFA for changes, combining biometrics, device pushes, and AI to detect anomalies like unusual call times.
- Conduct Regular Social Engineering Training: Simulate vishing attacks to train staff, especially in outsourced teams. M&S implemented post-breach refreshers to spot urgency tactics.
- Leverage Enterprise Password Managers: Tools like LastPass auto-generate unique credentials and rotate them only after incidents, not routinely.
- Audit Third-Party Vendors Thoroughly: Require penetration tests and shared incident response plans for partners like TCS.
| Old Password Policy | New Recommended Approach | Benefits in Preventing Breaches |
|---|---|---|
| 90-day forced resets | Event-based rotations | Reduces user fatigue and weak passwords by 50% |
| Phone/Q&A verification | Biometric + MFA pushes | Blocks 95% of impersonation attempts |
| Manual helpdesk scripts | AI anomaly detection | Identifies suspicious calls in real-time |
| Password-only access | Passkeys and zero-trust | Eliminates phishing entry points entirely |
Lessons from the Marks and Spencer TCS Cyber Attack
The £300 million loss from one fake call is a wake-up for retailers and beyond. As CEO Stuart Machin noted, the attack was “highly sophisticated,” yet rooted in basic human error. With Scattered Spider active, businesses must prioritize resilient password policies over outdated routines.
For consumers, the takeaway is simple: Enable MFA, use unique passwords, and stay vigilant. In cybersecurity, one proactive step can prevent millions in regret. As M&S rebuilds trust, the industry watches—will this breach spark lasting change?
Alex Rivera covers cybersecurity and the digital economy for Global Tech Review. Reach him at alex.rivera@globaltechreview.com.













